The aim of this project is to create a novel threat intelligence model and mechanism of exchange to accommodate Operational Technology (OT) and Internet of Things (IoT) in the Threat Intelligence Sharing (TIS) domain.
The TIS domain has been more IT-centric thus the need for the inclusion of threat intelligence models and mechanism of exchange is paramount. The objective of this project is as follows:
The architecture (Figure 1) shows CIC-PolyglOT, which is a data exchange mechanism for OT and IoT. The figure below shows applications that have been containerized using Docker. CIC-PolyglOT receives REST-based requests for remediation using customized STIX objects that were created from identified data objects.
CIC-PolyglOT translates the message into the required OT-based protocols and forwards them to the field devices. The TAXII Client receives TAXII requests that contain custom STIX objects from the TAXII Server and then forwards them to CIC-PolyglOT.
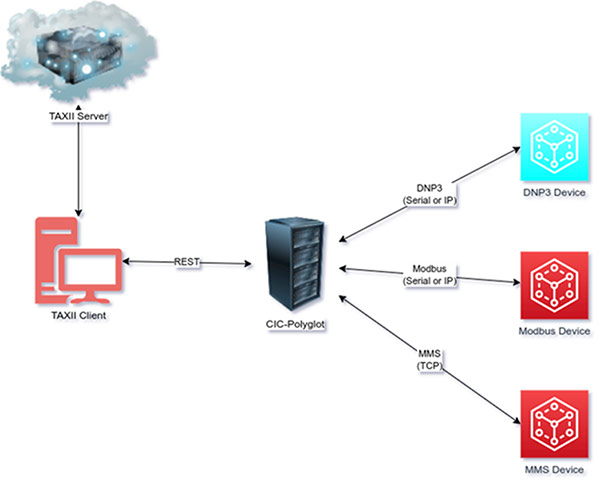
Currently, all the devices are Docker applications. The TAXII Server was created using cti-taxii-server and the TAXII server was created using taxii2-client. CIC-PolyglOT can be found at the CIC GitHub repository. DNP3, Modbus and MMS devices were created using openDNP3, modbus-tk and libiec61850 respectively.