The focus of this research is on creating a realistic IIoT dataset enriched with synchronized sensor and network data, complemented by a novel feature selection method to enhance anomaly detection accuracy while minimizing resource usage—bringing academic advances closer to practical IIoT security solutions.
Main contributions:

Developing a realistic IIoT testbed is a complex undertaking due to the heterogeneity of devices, communication protocols, and the substantial financial and technical resources required. Simulations or small-scale setups often fail to reflect the nuanced behaviors of real deployments. To address this gap, the Canadian Institute for Cybersecurity (CIC) established a dedicated IoT and IIoT laboratory featuring a sophisticated network infrastructure and 40 interconnected devices. These include over 15 types of industrial sensors built from scratch using Arduino boards alongside real industrial sensors, as well as network equipment, IoT devices, edge devices, and attacker systems—together providing a rich environment for experimentation.
The proposed testbed architecture is composed of five primary layers: the IoT/IIoT Layer, Network Infrastructure, Edge Layer, Cloud Layer, and Attacker Layer. By integrating diverse device types across these interconnected layers, the testbed replicates the complexity and heterogeneity of industrial environments, supporting comprehensive research into anomaly detection, intrusion detection, and resilience mechanisms in IIoT systems.
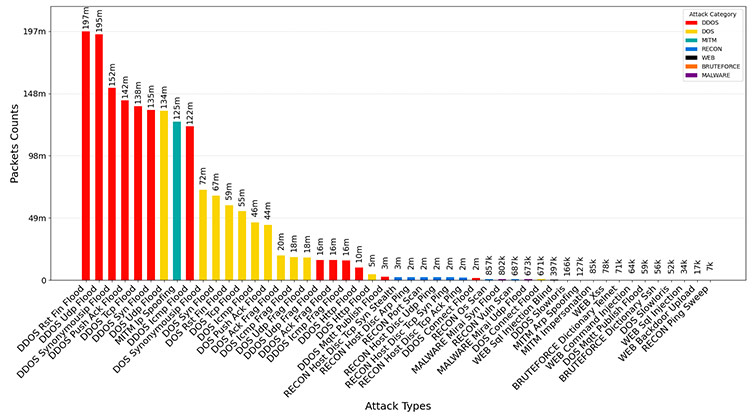
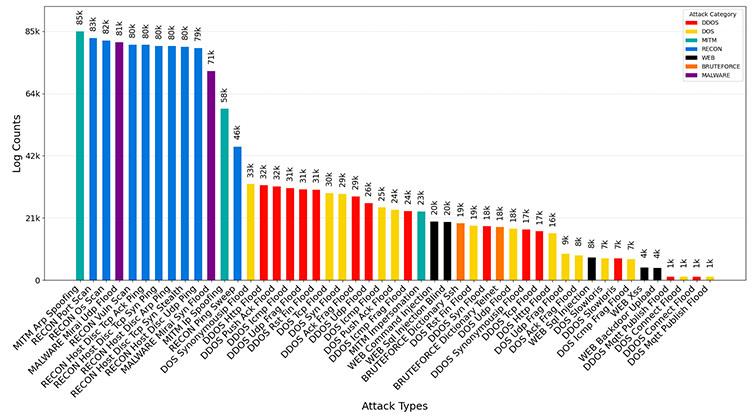
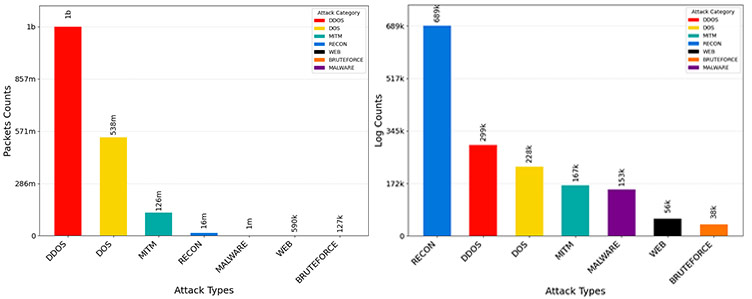
The authors would like to thank the Canadian Institute for Cybersecurity (CIC) for its financial and educational support.
Firouzi, A.; Dadkhah, S.; Maret, S.A.; Ghorbani, A.A. "DataSense: A Real-Time Sensor-Based Benchmark Dataset for Attack Analysis in IIoT with Multi-Objective Feature Selection." Electronics, 14, 4095, 2025.