The goal of this work is to contribute to ongoing cybersecurity research on electric vehicle charging stations by generating and publishing a dataset containing benign and attack scenarios. The attack scenarios include network and host attacks on the EV charger (Electric Vehicle Supply Equipment – EVSE) in both idle and charging states. Network attacks consist of various Reconnaissance and Denial-of-Service (DoS) attacks, while host attacks include Backdoor and Cryptojacking. The main contribution of this research are:
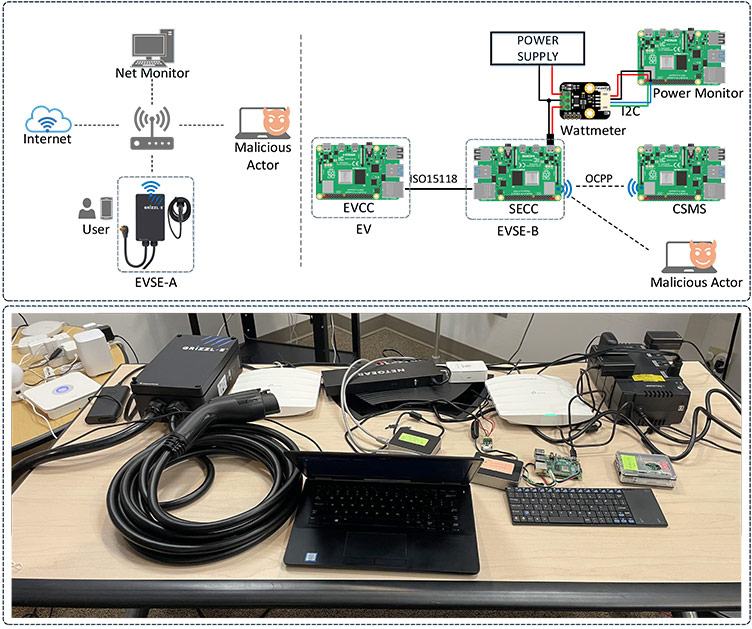
The testbed configuration setup comprises of an operational Level 2 charging station, EVSE-A, a Raspberry Pi and communication equipment. Raspberry Pis are used for the implementation of the Electric Vehicle Communication Controller (EVCC), EVSE-B, Power Monitor, and the local Charging Station Monitoring System (CSMS). The EVSE-A is configured to communicate with the remote CSMS platform using OCPP protocol. EVSE-B communicates with the EVCC and the local CSMS using ISO15118 and OCPP respectively. The power consumption of the EVSE-B is also monitored by another Raspberry Pi using a wattmeter and I2C protocol.
The dataset comprises three main data sources:
The table provided below outlines the labeling scheme employed for the host and power consumption dataset that has already been processed and utilized in the associated paper publication. This serves as a guide when using the individual unprocessed CSV files.
| Column ID | Entry |
|---|---|
| State | Idle, Charging |
| Scenario | Recon, DoS, Cryptojacking, Backdoor, Benign |
| Attack | Cryptojacking, Backdoor, None (ie. Benign), tcp-port-scan, service-version-detection, os-fingerpriting, aggressive-scan, syn-stealth-scan, vulnerability-scan, slowloris-scan, upd-flood, icmp-flood, pshack-flood, icmp-fragmentation, tcp-flood, syn-flood, synonymousIP-flood |
| Label | Attack, Benign |
| Interface | OCPP, ISO15118 |
Note:
The power consumed by the main board or Secondary Equipment Communication Controller (SECC) of the EVSE is largely not monitored by the CSMS. However, this data might serve as a good Indicator of Compromise. We use the I2C wattmeter to monitor and log the power consumed by the EVSE-B (raspberry pi) under benign and attack conditions. The dataset for benign and all attack scenarios are labelled combined into one CSV file. Dataset Features:
| Feature | Description |
|---|---|
| Time | Timestamp of sample |
| Shunt_voltage (mV) | Voltage drop that occurs across a shunt resistor of I2C Wattmeter |
| Bus_voltage | DC Voltage supply |
| Current_mA | EVSE-B Current consumption |
| Power_mw | EVSE-B Power consumption |
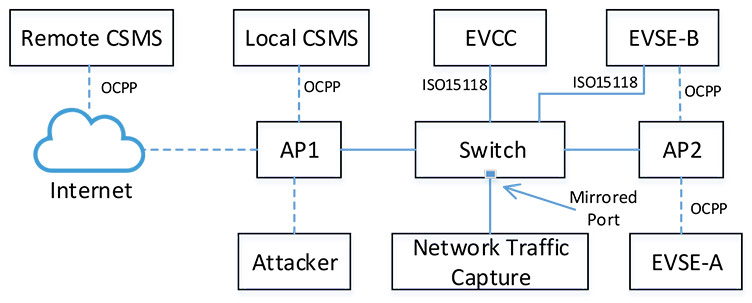
The complete network traffic captures for benign and attack scenarios are presented as .pcap files. The NFStream python library has been used to extract subsets of the traffic flow samples from the original pcap file as an example. The sample python script for pcap to CSV conversion has been added to the directory, this can be extended for more feature extraction. The network topology diagram is presented below.
Electric Vehicle Chargers, or EVSE, utilize resource-constrained or embedded computing hardware, such as its main board or SECC, to execute crucial intelligent functions required for charging station operations. Traditional host security solutions, like Anti-Virus software, may not be suitable for these resource-constrained devices. As an alternative, an effective solution harnesses the computing events of the system hardware to establish robust security measures.
Modern processors from manufacturers such as Intel, ARM, and AMD are equipped with Hardware Performance Counters (HPC) that record low-level microarchitecture events. These hardware events play a vital role in establishing baseline behavioural fingerprinting of devices, classifying malware, and applying machine learning techniques for anomaly detection. We utilize PERF to collect approximately 900 kernel and HPC events from the Raspberry Pi (EVSE-B) during the experimental scenarios. The table below presents some HPC and kernel events in this dataset. Refer to the readme file for the complete list of events.
| HPC Event | Description |
|---|---|
| instructions | Number of instructions executed |
| cache-misses | Number of cache misses |
| exc taken | Exception taken |
| cpu-migrations | CPU Migrations |
| dTLB-store-misses | Data TLB - Write Misses |
| l1d_cache_wr | Level 1 data cache access - Write |
| L1-icache-loads | Level 1 instruction cache access - Read |
| l2d_cache_rd | Level 2 data cache - Read |
| Mem_access_rd | Data memory access - read |
| Mem_access_wr | Data memory access - write |
| Kernel Events | Description |
|---|---|
| kmem kfree | Kernel memory freeing event |
| Net_dev_xmit | Network device transmission event |
| Qdisc_dequeue | Dequeue event |
| Raw_syscalls_sys_enter | System call entry (raw) event |
| Irq_softirq_raise | Software interrupt - Raised |
| Sched_migrate_task | Task migration event in the scheduler |
| Sched_switch | Task switch event in the scheduler |
| Syscalls_sys_enter_close | System call entry for close syscall |
| Syscalls_sys_enter_read | System call entry for read syscall |
| Syscalls_sys_enter_write | System call entry for write syscall |
The dataset contains some processed and labelled CSV files extracted from the original samples. The original individual CSV files, however, contains all samples captures for each scenario over extended amount of time.
The CICEVSE2024 dataset directory contains three subdirectories:
The authors would like to thank the Canadian Institute for Cybersecurity (CIC) for its financial and educational support.
E. D. Buedi, A. A. Ghorbani, S. Dadkhah, and R. Ferreira. “Enhancing EV Charging Station Security Using A Multi-dimensional Dataset : CICEVSE2024”. - (Submitted to ESORICS 2024 Conference).